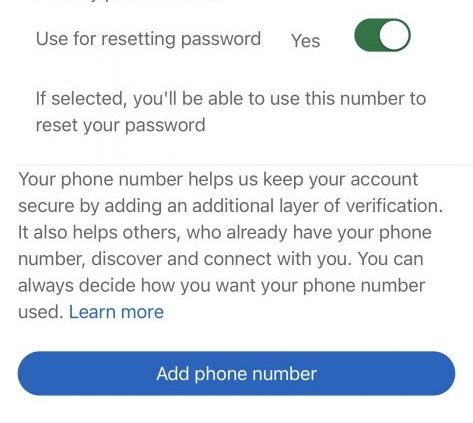
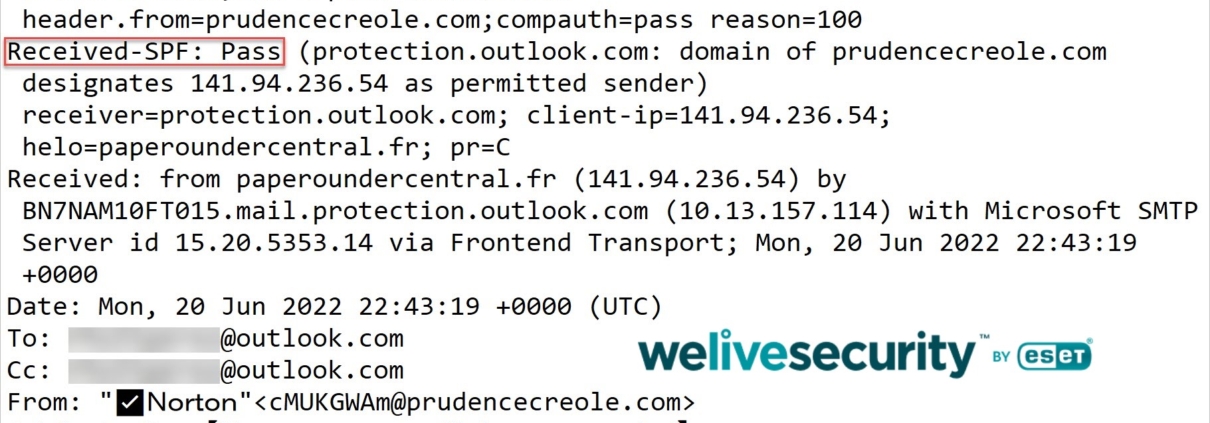
You may not be able to disappear completely from the internet, but you can minimize your digital footprint with a few simple steps
The post Is your personal data all over the internet? 7 steps to cleaning up your online presence appeared first on WeLiveSecurity